Executive Summary
The SOAR (Security Orchestration, Automation and Response) model, long presented as the heart of SOC automation, is now entering a phase of accelerated obsolescence.
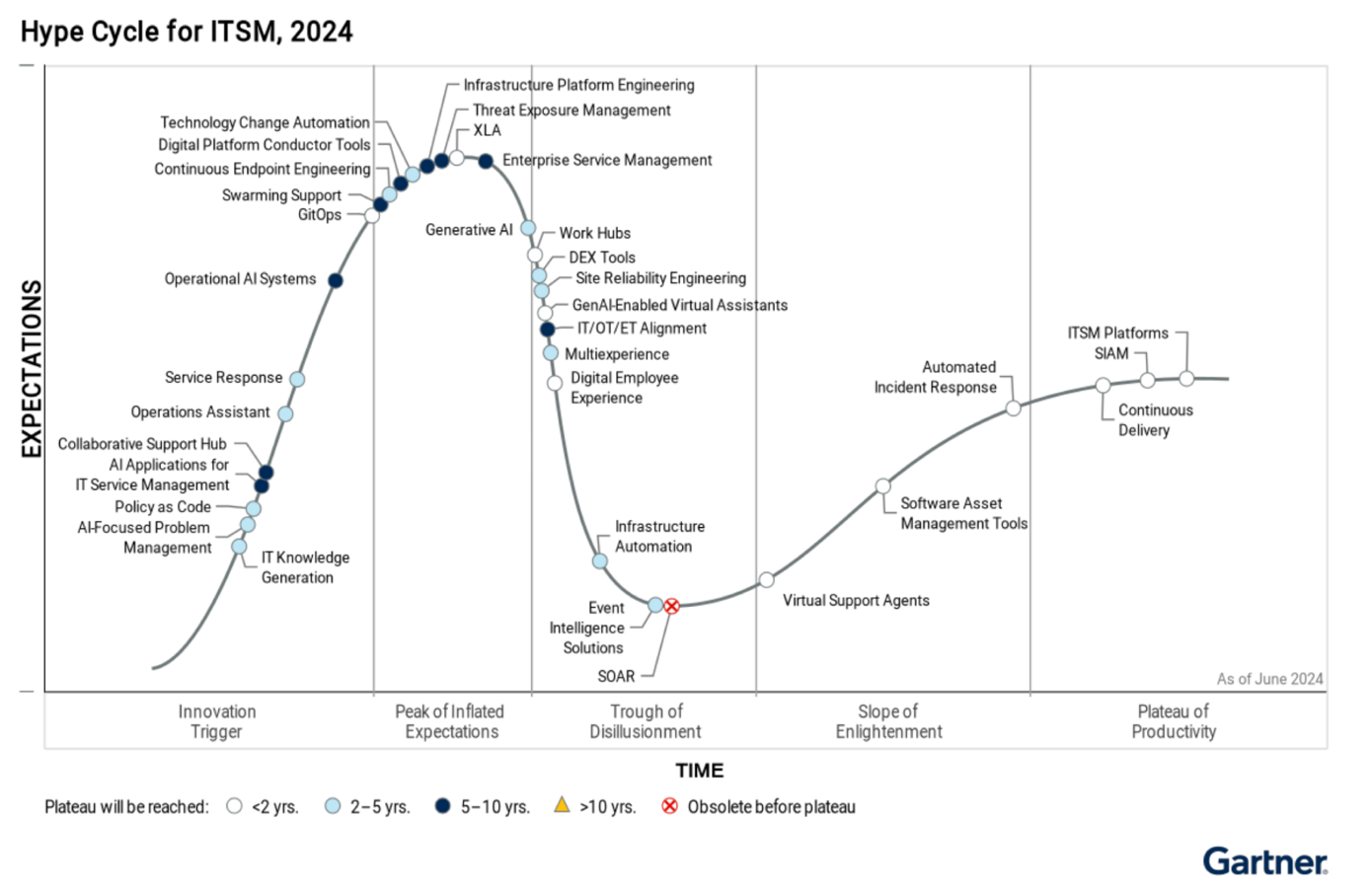
In 2024, Gartner classified it as “obsolete before plateau”, signaling that the market has not reached maturity before being overtaken by more integrated architectures: augmented SIEM/XDR, CTEM (Continuous Threat Exposure Management) and specialized AI agents.
This article presents the structural reasons for this evolution and the operational alternatives to favor for organizations seeking to modernize their security posture.
1. What is a SOAR?
SOAR was designed to automate and orchestrate incident responses through playbooks, in order to reduce MTTR (Mean Time To Respond) and standardize SOC actions.
The principle: when an event is detected by the SIEM, the SOAR automatically executes a series of preconfigured steps: enrichment of alerts, opening of tickets, isolation of a workstation, blocking of IP address, notification of analysts.
Its initial ambition: to replace manual gestures with automated workflows, increase productivity, and reduce dependence on scarce cybersecurity skills.
For a time, this promise seemed tenable: a cross-functional orchestration capable of transforming the SOC into a “cyber execution center.”
2. The SOAR model: promise and reality
The first use cases targeted low-criticality, high-recurrence incidents: phishing, EDR detection, simple network alerts.
But scaling up to complex scenarios has proven difficult: each integration requires specific API connectors, tailored scripts, and ongoing maintenance.
Actual benefits observed:
- 30-40% MTTR gains in basic use cases.
- Reduced load on Level 1 analysts.
- Standardization of response procedures.
However, according to data collected by several vendors and firms, less than 25% of SOCs are exploiting more than 50% of their SOAR capabilities after 18 months of integration.
The gap between promise and reality has widened: the cost of ownership (TCO) has often exceeded the operational benefits.
3. Why is SOAR running out of steam?
3.1. Gartner ranking: “Obsolete before plateau”
This ranking reflects an overall observation: the SOAR model has not found its balance between automation and contextualization.
Organizations have encountered barriers to adoption: deployment complexity, workflow rigidity, dependence on scripting experts.
In fact, innovation has shifted to the orchestration layers integrated into modern SIEM and XDR.
3.2. Competition from integrated SIEM/XDR
Next-generation SIEMs (Splunk, Microsoft Sentinel, Chronicle, QRadar, etc.) and XDRs now natively integrate automation modules: creation of visual playbooks, conditional triggers, direct integration with telemetry sources.
The result: The value of SOAR as an intermediary layer is fading. Organizations no longer need a third-party tool to execute automated actions; everything is already embedded.
3.3. Rigidity and technical debt
SOAR playbooks are static: they assume known and predictable flows.
However, hybrid and multi-cloud environments produce increasingly dynamic incidents with multiple dependencies.
Constant updates to third-party APIs require costly maintenance.Constant updates to third-party APIs require costly maintenance.
Constant updates to third-party APIs require costly maintenance.
4. Structural limits of SOAR
4.1. Integration complexity
Every API connector must be tested, secured, and versioned.
A simple update to an EDR or firewall can invalidate entire playbooks.
Maintenance becomes a project in its own right.
4.2. Lack of contextualization
SOAR operates according to static rules. It does not “understand” the threat context or the business criticality of the impacted asset.
This generates false positives that are executed automatically, and therefore increased operational risk.
4.3. Limited ROI
Between licensing, integration, and maintenance, the overall cost often exceeds several hundred thousand euros.
Efficiency gains are concentrated on repetitive use cases.
Few departments can justify such an investment in a logic of global transformation of the SOC.
5. Alternatives to SOAR
Alternatives to SOAR: towards an integrated and intelligent model
5.1. Native orchestration in SIEM/XDR
Modern platforms have native automation capabilities:
- Visual workflows based on event triggers.
- Python/Logic Apps scripts without third-party infrastructure.
- Direct integration of EDR, IAM, M365, Cloud actions.
These “intra-platform” orchestrations remove the dependency on an external SOAR engine, while improving resilience and governance.
They are part of a unified SOC model, where correlation, detection and response share the same analytical layer.
5.2. CTEM : Continuous Threat Exposure Management
CTEM, a concept promoted by Gartner since 2023, extends security logic beyond reaction.
It involves continuously assessing exposure surfaces, linking vulnerabilities, assets and exploitable attack scenarios.
This approach transforms the security posture: instead of waiting for the incident, the company acts on its exposure surface in real time.
In this context, automation is no longer just about response, but about proactively reducing risk.
5.3. Augmented AI and SOC agents such as Socrate.pro
The emergence of specialized AI agents marks a turning point: these models orchestrate actions no longer according to a script, but according to contextual reasoning.
They cross-reference logs, topology, business priorities and threat models to propose — or even execute — appropriate responses.
Exemples :
- Suggestion for intelligent isolation of an endpoint based on its criticality.
- Automatic enrichment of an IOC with confidence score.
- Natural language incident reporting.
These agents reduce reliance on fixed playbooks and provide continuous adaptation, essential in a modern SOC.
6. Field feedback
Customer feedback converges:
- SOAR projects take an average of 12 to 18 months to reach minimum maturity.
- Less than a third of organizations manage to automate more than 20% of their real-world use cases.
- SOCs that have migrated to native orchestrations or AI agents are seeing processing speed gains of 2 to 3 times.
Security teams now prefer to invest in SOC/SIEM/XDR convergence and augmented monitoring, rather than in an isolated automation brick.
7. Implications for COMEX and CISO management
For a decision maker, the question is no longer “do I need SOAR?” but “which detection-response architecture will maximize my ROI?”
Priorities are being redefined around:
- Agility: real-time adaptation to hybrid environments.
- Efficiency: native automation, without integration debt.
- Compliance: traceability and auditability of each automated action.
- Sustainability: compatibility with cloud-first and AI-native architectures.
In this paradigm, alternatives to SOAR are not replacements, but a logical evolution towards a unified, orchestrated, and contextual SOC.
Management must lead this transition by coordinating IT departments, CISOs and data engineering, in order to transform security into a performance lever and not a technical silo.
8. Key points to remember
- SOAR is officially classified as “obsolete before plateau” by Gartner (2024).
- Adoption barriers are linked to the complexity, cost and rigidity of playbooks.
- Modern SIEM/XDRs natively integrate orchestration functions.
- The CTEM offers a proactive posture based on measuring the risk of exposure.
- AI agents enable adaptive, contextualized and explainable automation.
The future of SOC is AI-native, integrated and outcome-driven.
SOAR Hype Cycle (Gartner 2024)
FAQ
Is SOAR totally outdated?
No, it still has occasional relevance in legacy or highly compartmentalized environments. But its role is reduced to specialized orchestration functions.
What are the best alternatives to SOAR?
Orchestrations integrated into SIEM/XDR, complemented by a CTEM approach and decision-making AI agents, represent the most sustainable path today.
What ROI can you expect from a migration?
A 50% reduction in MTTR and an average 30% gain in analyst load, thanks to the elimination of integration layers.
What recommendations for a COMEX?
Prioritize integrated architecture, invest in data governance and traceability, align tools with the ISO 27001 standard and anticipate the convergence between analysis, decision and AI-native execution.
SOAR in 2025: obsolescence, limits and alternatives